Threat and Risk Assessment
Organizations and people face a widening range of cyber threats in the ever-developing digital ecosystem, which have the ability to disrupt operations, damage sensitive data, and erode confidence. A crucial step in cybersecurity is the threat and risk assessment (TRA), which aids in identifying, assessing, and prioritizing possible dangers. Stakeholders may adopt efficient security measures and protect crucial assets by making well-informed decisions by knowing the risks encountered and their corresponding weaknesses. This article explores the idea of threat and risk assessment, as well as its significance, methodology, and role in creating a robust cybersecurity posture.
How does a threat and risk assessment work?
A methodical technique to assess possible threats and vulnerabilities that might have a negative influence on an organization’s information assets, systems, or operations is known as threat and risk assessment. The main objective of TRA is to categorize and rank risks, enabling organizations to allocate resources effectively and concentrate on areas that demand immediate attention.
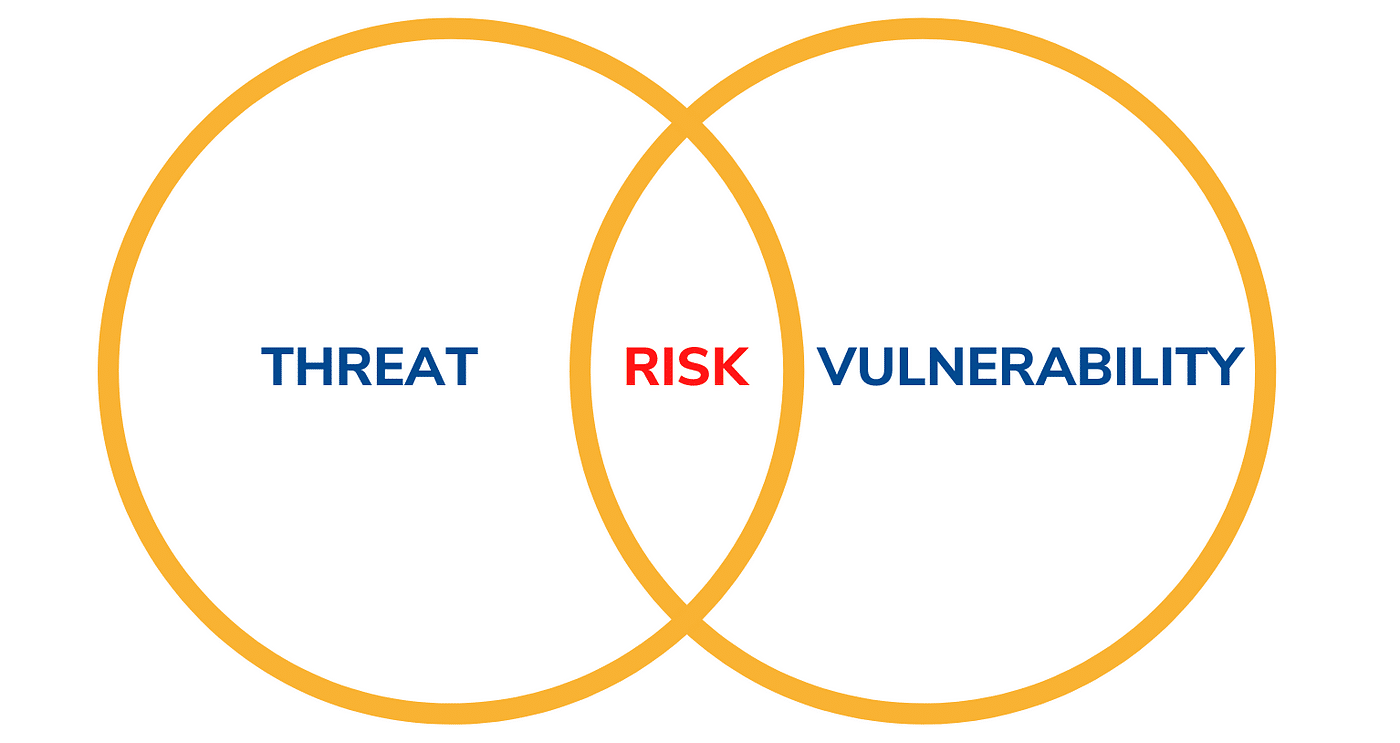
Any prospective occurrence or scenario that may result in unauthorized access to, use of, disclosure of, interruption of, alteration of, or destruction of information or systems is seen to be a threat. Threats might be harmful, like cyberattacks, or benign, like natural catastrophes or human mistake.
On the other hand, a risk is the chance and consequences of a danger taking advantage of a weakness inside a system or organization. Threat actors can carry out attacks by taking advantage of security measures’ flaws or gaps, or vulnerabilities. Threats are identified, their potential impact is evaluated, and the efficacy of current controls or countermeasures to manage those risks are evaluated as part of the TRA process.
- Threat and risk assessment are important.
Threat and Risk Assessment is critical to cybersecurity for a number of reasons, including:
1. Setting Resource Priorities: TRA aids organizations inefficient resource allocation. Decision-makers may invest in the right security measures and technology by being aware of the biggest dangers.
2. Data Breach Prevention: By proactively addressing information system vulnerabilities, organizations can lower the probability of successful cyber-attacks and data breaches.
3. Meeting Compliance Requirements: Risk assessment and mitigation are required by particular regulatory frameworks that apply to many sectors. Organizations are kept in compliance with pertinent laws and rules thanks to TRA.
4. Supporting Decision-Making: TRA equips decision-makers with the knowledge they need to assess their risk appetite and security investing options.
5. Enhancing Incident Response Preparedness: By being aware of possible threats and dangers, Security Guard Services may create thorough incident response plans that effectively lessen the effects of security incidents.
- Threat and Risk Assessment Methodologies
There are several approaches available for doing threat and risk assessments. Depending on their needs and available resources, Security Guard Services can select the approach that best suits them. Each methodology may have benefits and limitations. Some typical approaches include:
1. Qualitative risk assessment entails putting arbitrary values on hazards based on the likelihood, impact, and risk tolerance of the organization, among other considerations. Although lacking in quantitative accuracy, it offers a high-level awareness of dangers.
2. Quantitative Risk Assessment: This method evaluates hazards via the use of numerical values, frequently through the use of statistical analysis and data modeling. It offers a more exact and quantifiable evaluation of hazards.
- Threat and risk assessment: Challenges and Limitations
Threat and Risk Assessment is a useful procedure; however, it has significant drawbacks and restrictions:
1. Dynamic Threat Environment: It is difficult to always keep threat assessments up to date due to the constantly shifting cybersecurity environment.
2. Complexity: TRA may be a time-consuming and difficult procedure, particularly for big organizations with a wide variety of assets and processes.
3. Resource Constraints: Some organizations may not have the resources to conduct TRA since it needs knowledge, time, and other resources.
In the field of cybersecurity, conducting a threat and risk assessment is a critical practice that enables organizations to proactively detect and mitigate possible vulnerabilities and threats. Security company Toronto acquire a clear knowledge of their cybersecurity risks and deploy resources efficiently for risk mitigation by completing a thorough evaluation using proven procedures. Despite obstacles and constraints, adopting best practices and incorporating TRA into the entire company plan may boost cybersecurity, lower risk exposure, and improve the protection of important assets and data.